
Two Factor Authentication (2FA). What It Is and How to Set It Up in Linken Sphere
What is 2FA?
Two-Factor Authentication (2FA) is a method of enhancing account security by requiring user identity verification through two different authentication factors. Unlike traditional single-factor authentication, which only requires a password, 2FA involves additional steps, making it significantly harder for malicious actors to gain access.
When using 2FA, after entering the password, the system requests a second authentication factor. This is most commonly a one-time code sent to the user's mobile phone via SMS or generated by a dedicated application (such as Google Authenticator or Authy). Hardware tokens that generate codes or are inserted into the computer's USB port can also be used.
Popular Methods of Two-Factor Authentication (2FA) and How They Work
1. E-mail
How it works:
After entering the password on a website or application, the user receives a one-time code at the specified email address. This code must be entered in the appropriate field to complete the authentication process.
Advantages:
- Availability: Almost all users have email, and it does not require installing additional software.
- Convenience: Codes can be easily accessed through web interfaces or mobile email applications.
Disadvantages:
- Security: Email can be vulnerable to phishing and hacking, especially if the user has a weak password or lacks protection for their email account.
- Delays: Sometimes there can be delays in email delivery, slowing down the authentication process.
2. SMS Codes
How it works:
After entering the password, a one-time code is sent via SMS to the user's phone number. This code is entered into the appropriate field on the website or application to complete the authentication process.
Advantages:
- Simplicity:Easy to understand and use, does not require special applications.
- Wide Availability: Suitable for most users, as almost everyone has a mobile phone
Disadvantages:
- Vulnerability: Susceptible to SIM swapping attacks, where an attacker can take control of the phone number.
- Delays and Availability: SMS delivery delays are possible, especially with international transfers or network issues.
3. Authenticator Apps
How it works:
TThe user installs an authenticator app, such as Google Authenticator, Authy, or Microsoft Authenticator. The app generates one-time codes that the user enters along with the password to complete the authentication process.
Advantages:
- Security: More secure compared to SMS and email as they are not dependent on external services and vulnerabilities.
- Offline Access: Applications work without an internet connection, making them convenient for use in any conditions.
Disadvantages:
- Requirement for Installation: The user needs to install and set up the application on their device.
- Loss of Access: In case of phone loss or damage, restoring access may require additional steps, such as using backup codes or contacting support.
Reasons to Use 2FA
1. Enhanced Security
The main reason for using Two-Factor Authentication (2FA) is the significant increase in the security level of your accounts. Passwords can be stolen or guessed, especially if they are weak or frequently used across different sites. 2FA adds an additional layer of protection by requiring something only the user knows (password) and something they have (e.g., a one-time code).
2FA Provides Protection Against Various Types of Attacks
- Phishing: Even if an attacker learns your password through a phishing attack, they would still need the second factor to access the account.
- Keyloggers: Keyloggers record everything you type on the keyboard. But even if a password is stolen this way, the attacker would still need the second factor for access.
- Weak Passwords: Many users choose weak or easily guessable passwords. 2FA adds an additional line of defense, making it harder for attackers to gain access.
2. Availability and Ease of Implementation
Today, many major companies and services, such as Google, Facebook, Apple, and banking institutions, offer 2FA. Implementing this technology has become easier thanks to the availability of various methods, such as SMS, email, authenticator apps, and biometric data. This makes the use of 2FA accessible to a wide range of users.
Enabling Two-Factor Authentication (2FA) in Linken Sphere
Step 1: Go from the main screen to the account management page.
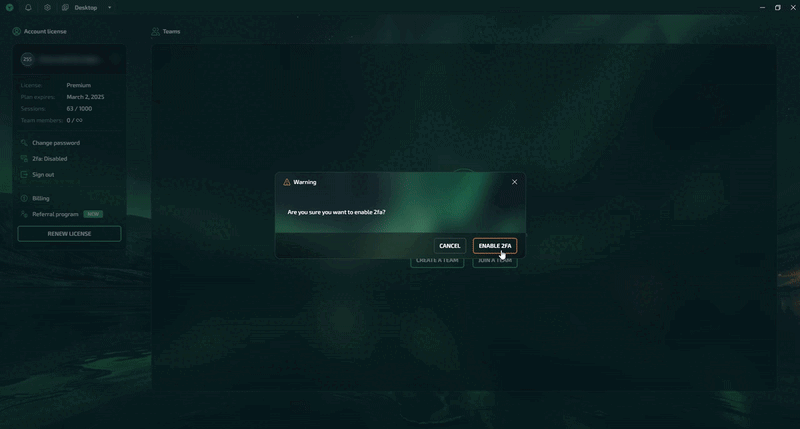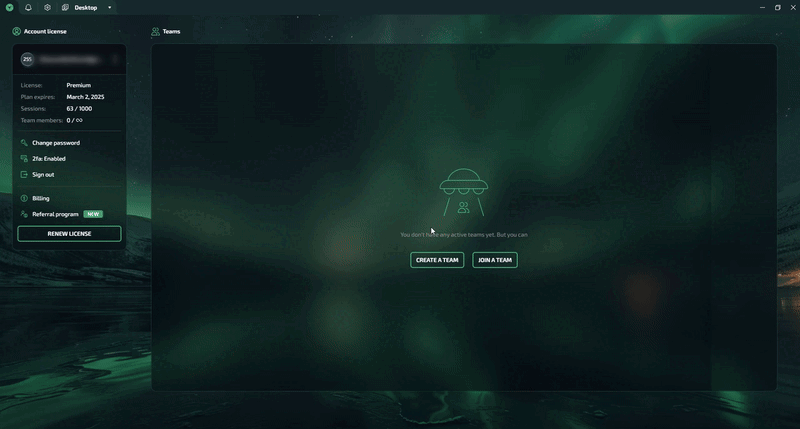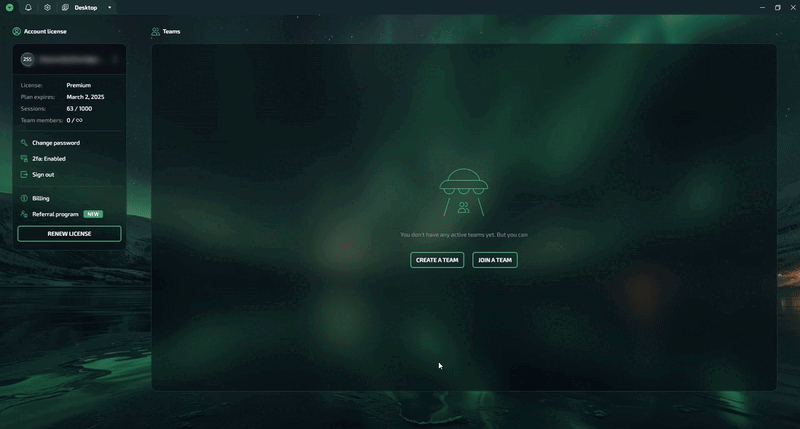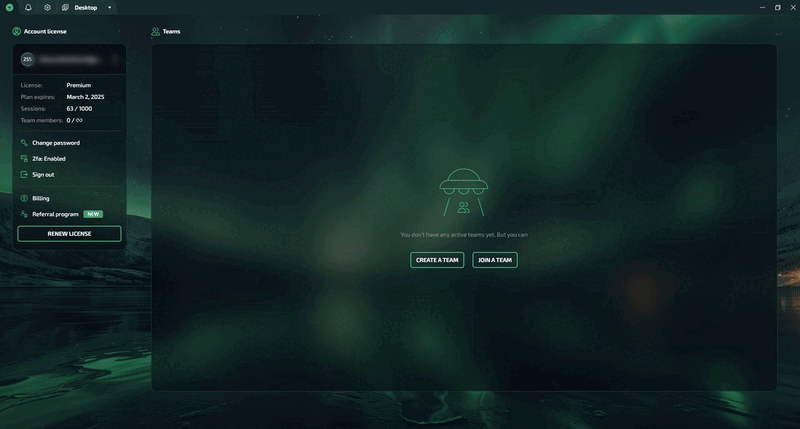
Step 2: Locate the option to open the account settings context menu and select '2FA: Disabled'.
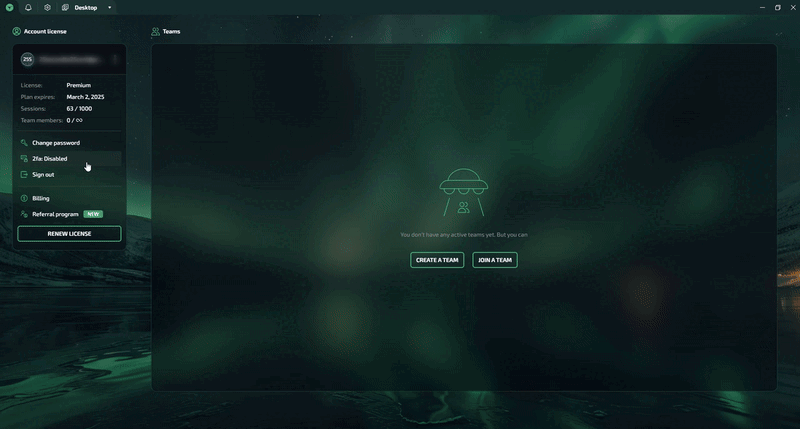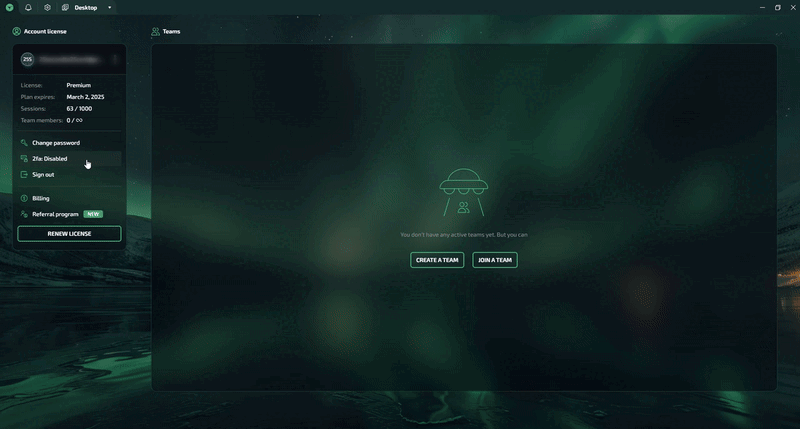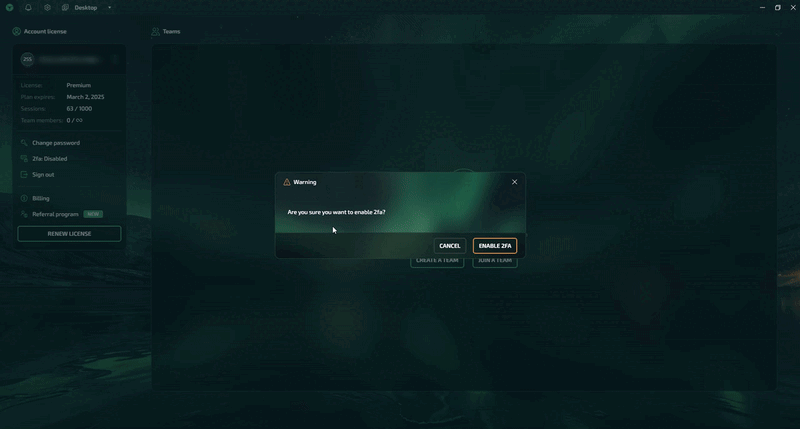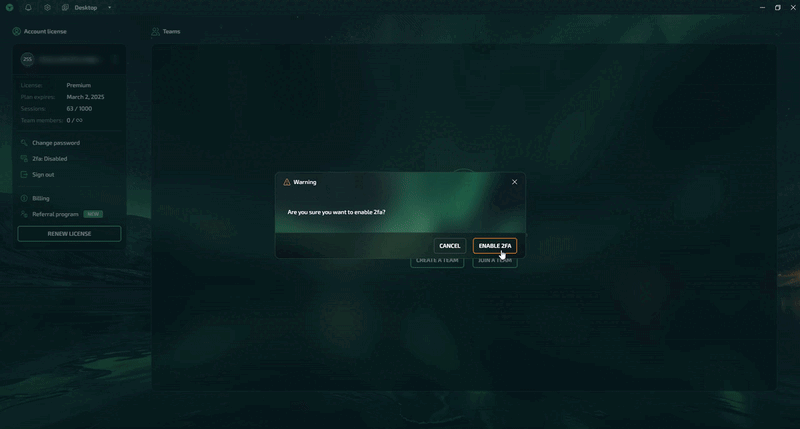
Step 3: Confirm the activation of 2FA.
2FA Verification:
Step 1: Launch the Linken Sphere browser and log into your account.

Step 2: Go to the page to enter the one-time code that will be sent to your email.
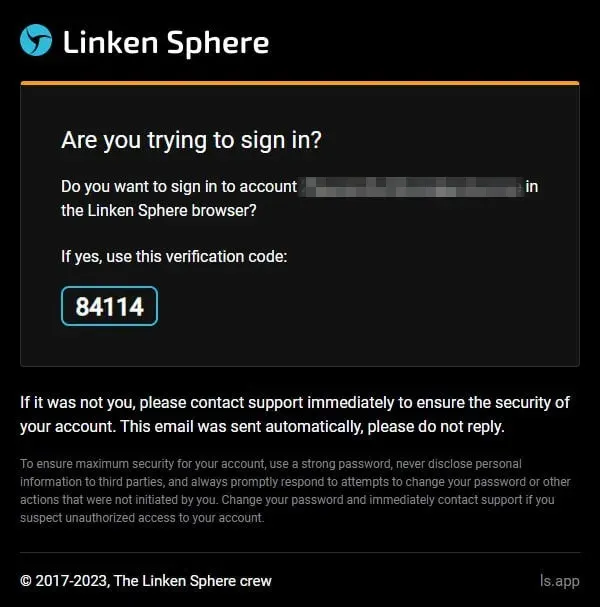
Example email with the code:
Step 3: Copy the code received in the email and paste it into the Linken Sphere window.
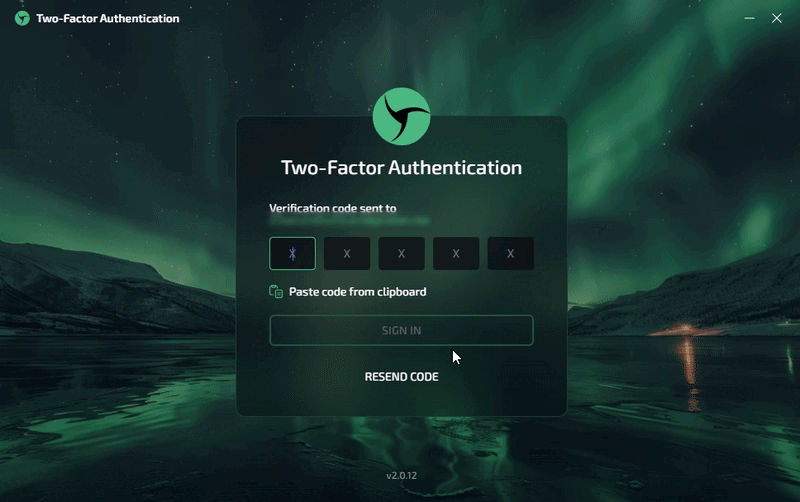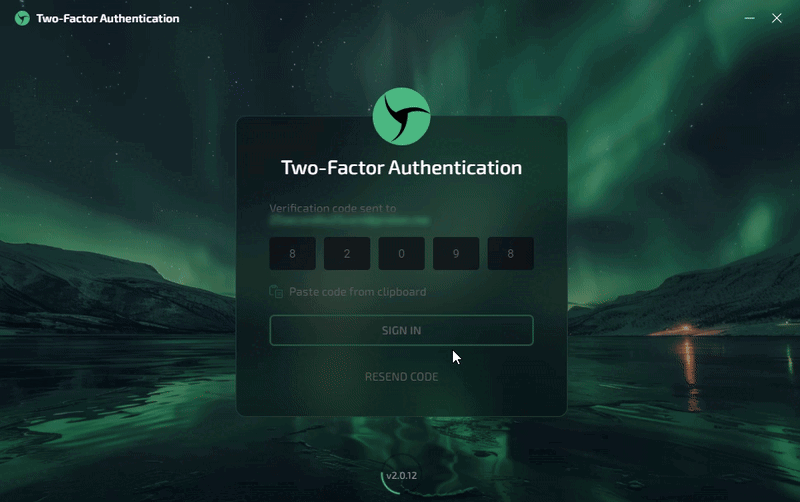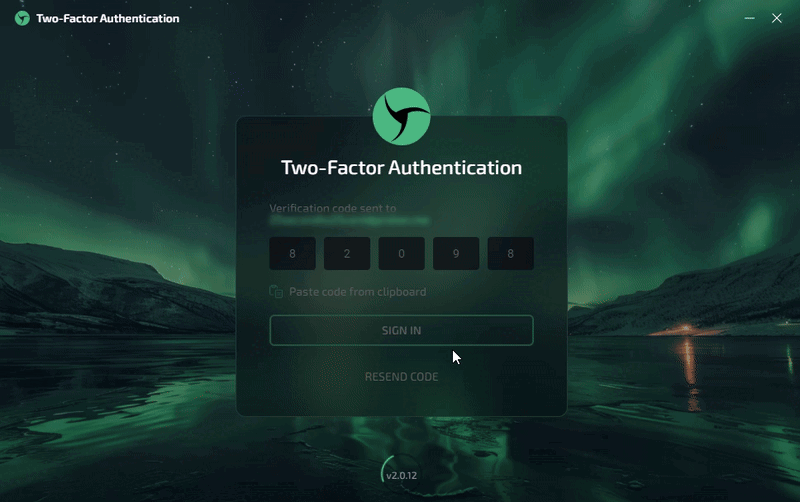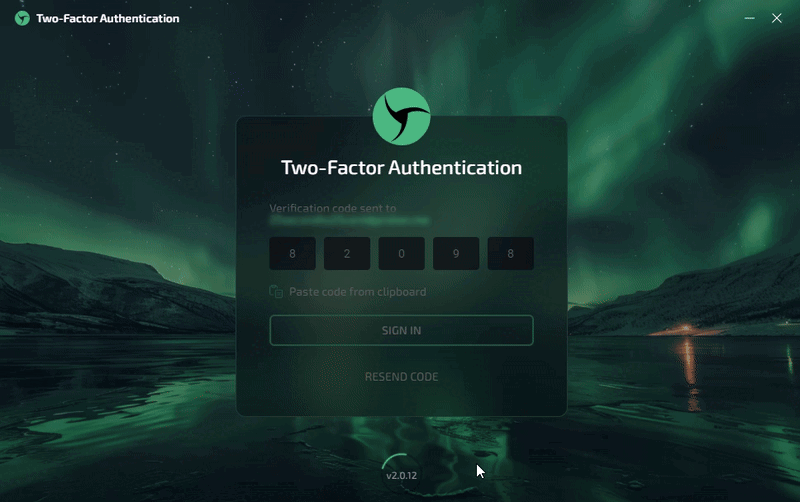
Step 4: After verifying the code, you will be redirected to the main page, ready to start working!
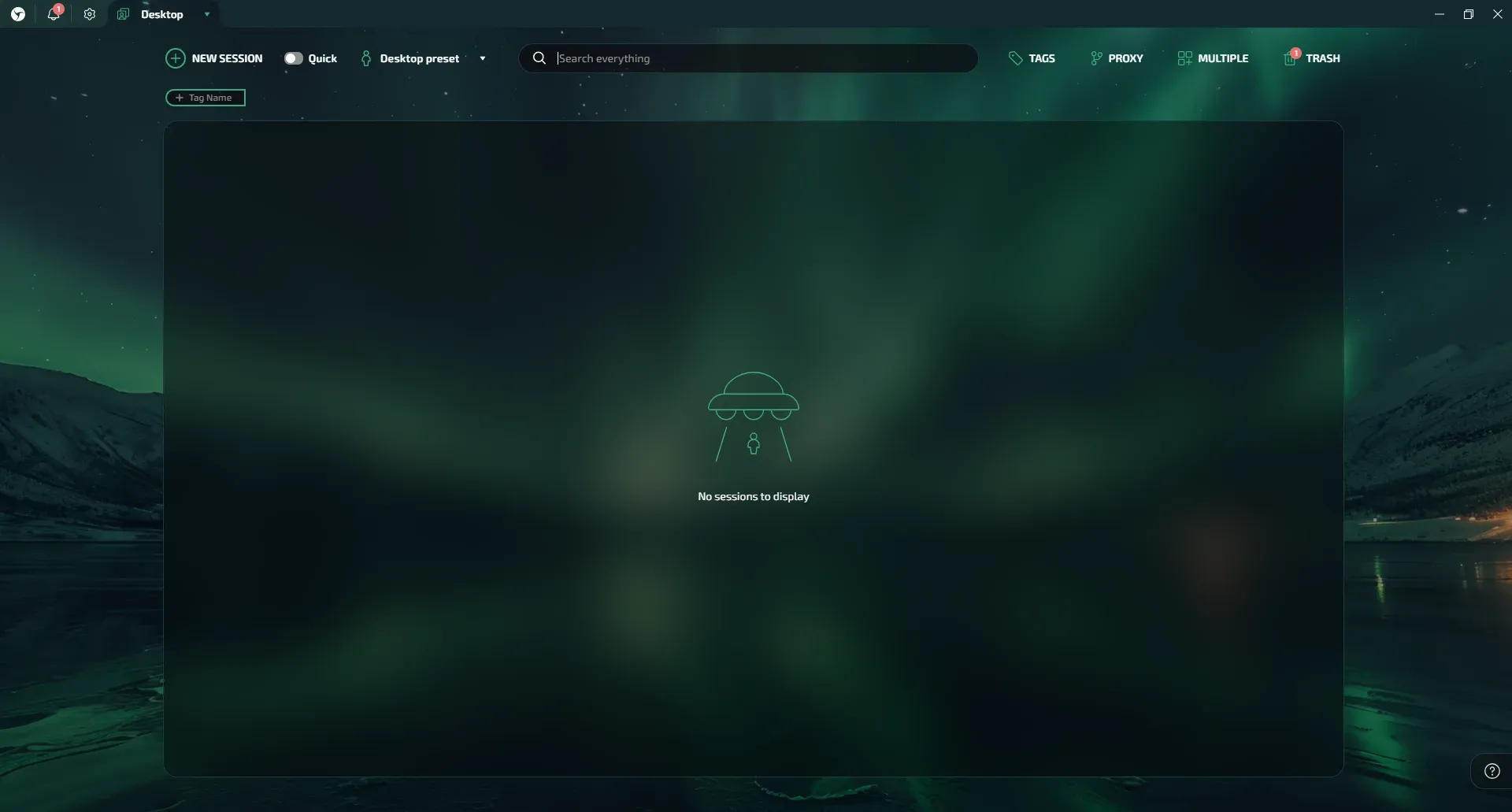
Now your Linken Sphere account is secured with an additional level of security thanks to two-factor authentication.
Summary:
This article provides a detailed overview of two-factor authentication (2FA), starting from defining this security method and ending with a practical guide on enabling it in the Linken Sphere browser.

Using LS with OBS Studio
This is a comprehensive guide that will help you implement video stream substitution in Linken Sphere without the risk of detection by anti-fraud systems.

Built-in Video Stream Spoofing in Linken Sphere
A couple of months ago, we released a detailed guide on using OBS Studio with Linken Sphere. Since then, we have received numerous questions about spoofing video streams using this software. Your activity has shown that native video spoofing functionality is truly in demand among users.

Why Google Blocks Accounts and What Your Antidetect Has to Do With It
Google has once again complicated the mechanisms of digital identification by deploying a new, more sophisticated layer of protection based on proprietary HTTP headers. This quiet change caught most of the market off guard, triggering a wave of rushed updates. While others hastily released superficial 'fixes', we realized that we were dealing not with a minor issue but with a fundamental shift that required deep and comprehensive analysis.