
Why Google Blocks Accounts and What Your Antidetect Has to Do With It
Introduction
Google has once again complicated the mechanisms of digital identification by deploying a new, more sophisticated layer of protection based on proprietary HTTP headers. This quiet change caught most of the market off guard, triggering a wave of rushed updates. While others hastily released superficial 'fixes', we realized that we were dealing not with a minor issue but with a fundamental shift that required deep and comprehensive analysis.
In this article, we’ll explain how this new tracking mechanism works. First, we’ll take a detailed look at the content and purpose of the key headers — from the X-Browser-* family to the critically important X-Client-Data and X-Chrome-Id-Consistency-Request — explaining exactly how they enable Google to distinguish a real user from an antidetect. Then we’ll present the results of our extensive research, showing without embellishment how leading antidetect browsers handle (or more often fail to handle) this new threat. If you’re already familiar with the theory, you can skip straight to our research results.
However, to truly understand why some solutions create a coherent and credible fingerprint while others only produce a mosaic of easily detectable artifacts, we strongly recommend reading the full analysis. The fine implementation details are precisely what separates stable operation from inevitable blocking.
Which headers are we talking about?
When interacting with its services, Google Chrome uses a set of proprietary HTTP headers that serve a dual purpose. Officially, they are intended for internal tasks such as A/B testing, telemetry collection, and browser authenticity verification. However, their actual use is much broader — they serve as a powerful mechanism for user identification and anomaly detection, making their analysis and emulation a key task for antidetect browser developers. Let’s examine them in more detail.
The X-Browser-* Family

// X-Browser-* headers //
X-Browser-Channel: stable
X-Browser-Year: 2025
X-Browser-Validation: XPdmRdCCj2OkELQ2uovjJFk6aKA=
X-Browser-Copyright: Copyright 2025 Google LLC. All rights reserved.This group includes 4 headers that serve to identify the browser build and verify its authenticity. In this way, Google determines that the request was made by a genuine Google Chrome browser rather than another browser trying to disguise itself as Chrome.
- X-Browser-Channel — informs the server about the release channel of the browser (stable, beta, dev, canary). This allows Google to adapt content or functionality depending on build stability. For most users, the value is stable.
- X-Browser-Year — the release year of the browser version used.
- X-Browser-Copyright — a standard string with copyright information.
- X-Browser-Validation — the most important header in this group, designed to protect against bots and modified clients. Its value is generated based on two components: the Chrome API key embedded in the binary file (unique for each OS) and the User-Agent string of the current request.
The X-Client-Data Header
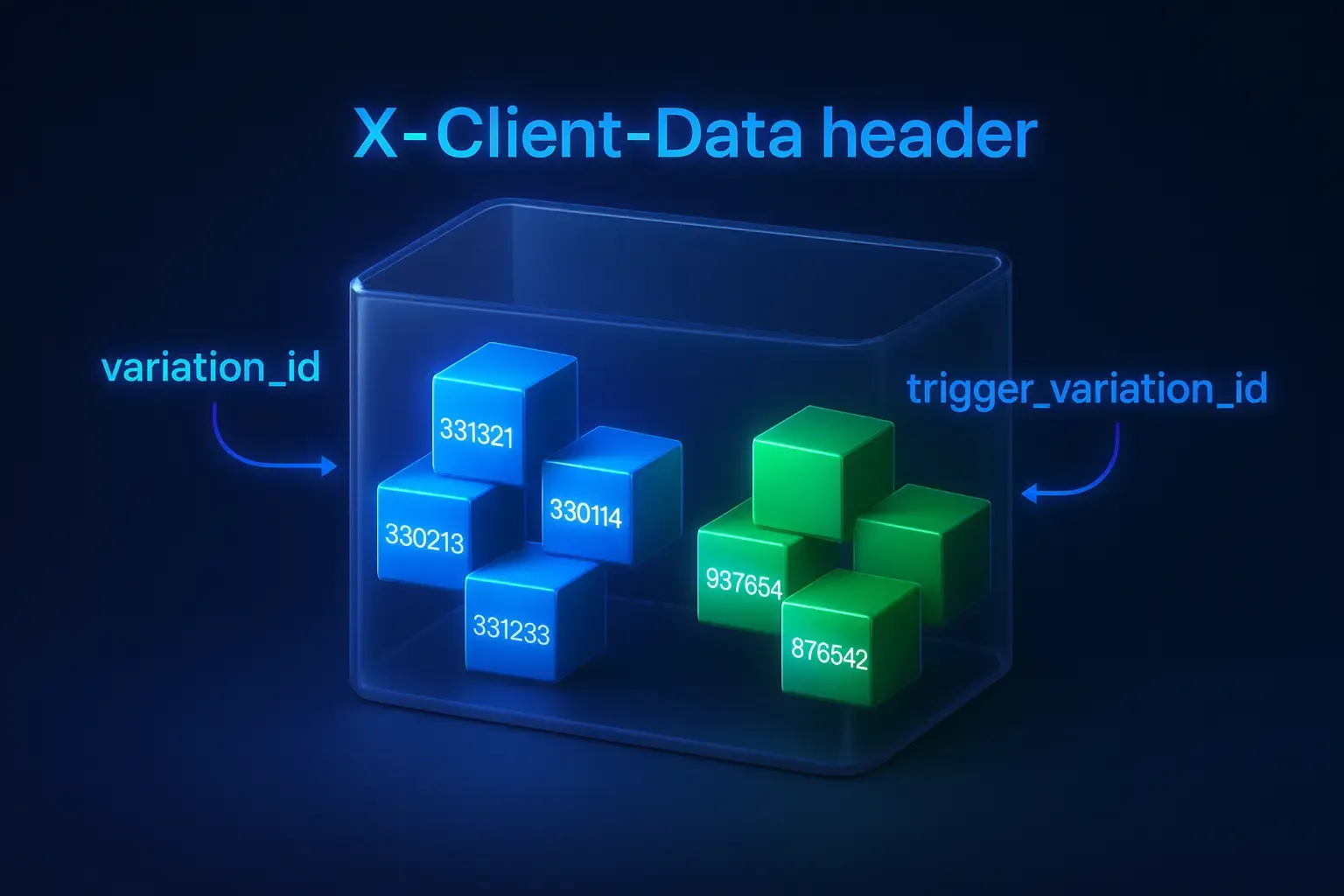
// X-Client-Data header //
x-client-data: CJa2yQEIpLbJAQipncoBCMvrygEIk6HLAQj0o8sBCIWgzQEI/aXOAQiTgc8BCP+EzwEIkIfPAQiFis8BCKqLzwEIpIzPARiYiM8BGIyJzwE=
Decoded:
message ClientVariations {
// Active Google-visible variation IDs on this client. These are reported for analysis, but do not directly affect any server-side behavior.
repeated int32 variation_id = [3300118, 3300132, 3313321, 3323339, 3330195, 3330548, 3362821, 3379965, 3391635, 3392127, 3392400, 3392773, 3392938, 3393060];
// Active Google-visible variation IDs on this client that trigger server-side behavior. These are reported for analysis *and* directly affect server-side behavior.
repeated int32 trigger_variation_id = [3392536, 3392652];
}X-Client-Data is a key tool in Google’s 'Field Trials' system, represented as a web-safe Base64-encoded protobuf object. It informs Google servers about which experimental features are active in a given browser instance, enabling large-scale A/B testing, gradual rollout of new features to limited user groups, and dynamic adjustment of web service behavior (e.g., Google Search or YouTube) for specific clients.
The message contains two main lists of numerical identifiers:
- variation_id — IDs of active experiment groups in the browser,
- trigger_variation_id — a separate list of IDs marked as 'trigger' for Google web properties. These values are determined at the first launch of a Chrome profile and may slightly vary between subsequent launches. Completely deleting the profile folder initiates their regeneration.
The key feature of this mechanism lies in its lifecycle: the variation values are determined at the first Chrome profile launch and may slightly change in future sessions. Fully deleting the profile folder causes them to regenerate. Thus, this header is not a static 'fingerprint' but a dynamic identifier unique to each profile.
The X-Chrome-Id-Consistency-Request Header
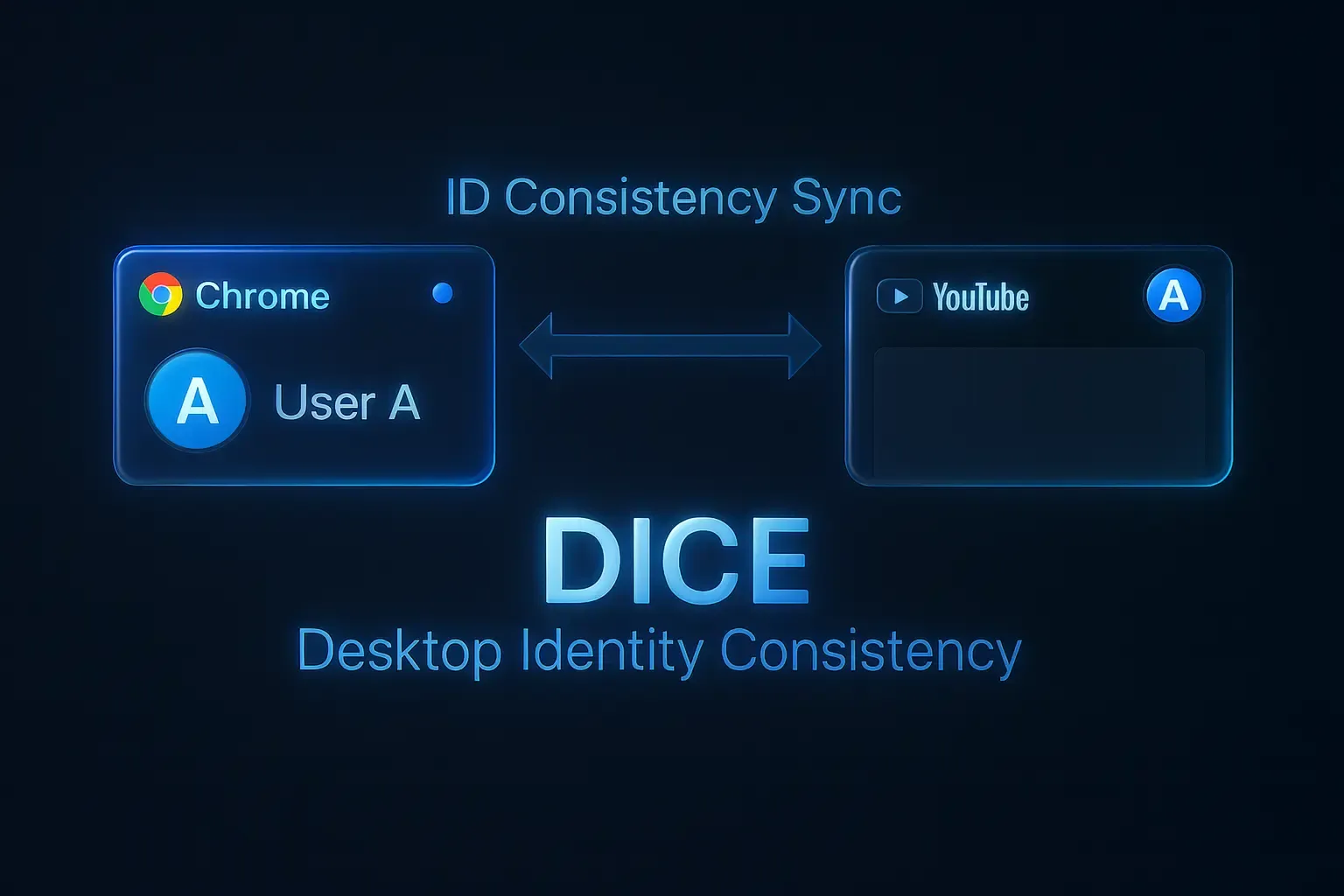
// X-Chrome-Id-Consistency-Request header //
x-chrome-id-consistency-request:
version=1,client_id=77185425430.apps.googleusercontent.com,device_id=78e64ade-1b2a-4ea6-9068-9765aa13e80a,signin_mode=all_accounts,signout_mode=show_confirmationX-Chrome-ID-Consistency-Request is a key element of the DICE (Desktop Identity Consistency) mechanism. Its main task is to ensure that the list of Google accounts you’re signed into in the browser matches the list of accounts active on Google web pages. In simpler terms, it’s a kind of consistency guarantee that Chrome presents to Google sites.
This header is sent with every request to Google domains associated with account management (such as accounts.google.com) and contains information about all active browser sessions. In response, the server returns the X-Chrome-ID-Consistency-Response header, which instructs the browser which accounts to add or remove on the web page to achieve full synchronization. This mechanism is why, when you add a new account in Chrome, it instantly appears in your list on YouTube without requiring another login.
Since the X-Chrome-Id-Consistency-Request header is tightly tied to the browser’s internal authentication system, its absence or incorrect formation is an obvious marker of emulation for Google. If it’s missing in requests to Google authentication services, it’s an easily verifiable sign that the client isn’t a standard Chrome user. This is an architectural flaw present in most antidetect browsers on the market, instantly exposing their inauthenticity.
Most antidetect solutions on the market fail to properly reproduce this mechanism. However, even its formal presence does not guarantee authenticity. In one of the products we reviewed, the account sync function was declared, and the header was indeed sent — but how accurately does it imitate real Chrome behavior? The details of this implementation hide new detection risks, which we’ll demonstrate in our research.
Research: How Popular Antidetects Emulate Chrome
Theory is the foundation, but the real picture of the market can only be seen in practice. To objectively assess how leading antidetect solutions emulate Chrome’s key mechanisms, we conducted our own in-depth research. Our analysis focused on two critical aspects: the correctness of the headers being sent and the quality of the Google account login implementation — an essential part of any modern browser.
And in keeping with our principle of transparency, we’ll describe the entire methodology in detail. This allows you not only to trust our results but to independently verify any antidetect browser and assess its reliability.
How to Check Your Antidetect Browser?
- Create a session/profile in your antidetect browser.
- Launch the session, wait 20–30 seconds (this is necessary for experiment groups to be assigned), then stop the session.
- Launch the session again.
- Open DevTools by pressing F12 > switch to the "Network" tab.
- Go to accounts.google.com.
- Check the headers in several requests to this domain.
- Repeat the procedure with 5 different sessions/profiles to reduce margin of error.
You should get a list of 6 headers similar to the following example:
// New Chrome Headers //
x-browser-channel: stable
x-browser-copyright: Copyright 2025 Google LLC. All rights reserved.
x-browser-validation: qSH0RgPhYS+tEktJTy2ahvLDO9s=
x-browser-year: 2025
x-chrome-id-consistency-request: version=1,client_id=77185425430.apps.googleusercontent.com,device_id=1efe3440-1559-4a46-b9f4-ea61f9a587b9,signin_mode=all_accounts,signout_mode=show_confirmation
x-client-data: CKy1yQEIkbbJAQiktskBCKmdygEI3vjKAQiSocsBCJGkywEIhqDNAQj9pc4BCPaEzwEI04jPAQiFis8BCJaMzwEIo4zPARiYiM8B
Decoded:
message ClientVariations {
// Active Google-visible variation IDs on this client. These are reported for analysis, but do not directly affect any server-side behavior.
repeated int32 variation_id = [3300012, 3300113, 3300132, 3313321, 3325022, 3330194, 3330577, 3362822, 3379965, 3392118, 3392595, 3392773, 3393046, 3393059];
// Active Google-visible variation IDs on this client that trigger server-side behavior. These are reported for analysis *and* directly affect server-side behavior.
repeated int32 trigger_variation_id = [3392536];
}Checking Google Account Authorization:
- Create a session/profile in your antidetect browser.
- Launch the session.
- In the top-right corner, click the profile icon.
- Check if the "Sign in to..." button is visible — if this button is present, Google account login is technically possible.
- Click it and log in to your Google account.
- Click the authorized account icon in the top-right corner > "Manage your Google Account".
- Go to "Security" > "Your devices" > "Manage all devices".
- Click the current device and, if necessary, confirm your account password.
- Pay attention to the device name visible to Google (displayed under the OS name).
Now you’ve collected all the necessary data — it’s time to draw a verdict. To structure your analysis and objectively assess your antidetect browser, compare your results with the checklist below. The more positive answers you get, the higher the quality of the emulation, and the harder it will be for Google’s systems to distinguish you from a genuine user.
- Does the browser send all X-Browser-* headers?
- Does the browser send the X-Client-Data header, and does it contain more than one variation_id?
- Does the browser send the X-Chrome-Id-Consistency-Request header and support Google account login?
- Does the device name shown during Google login look realistic?
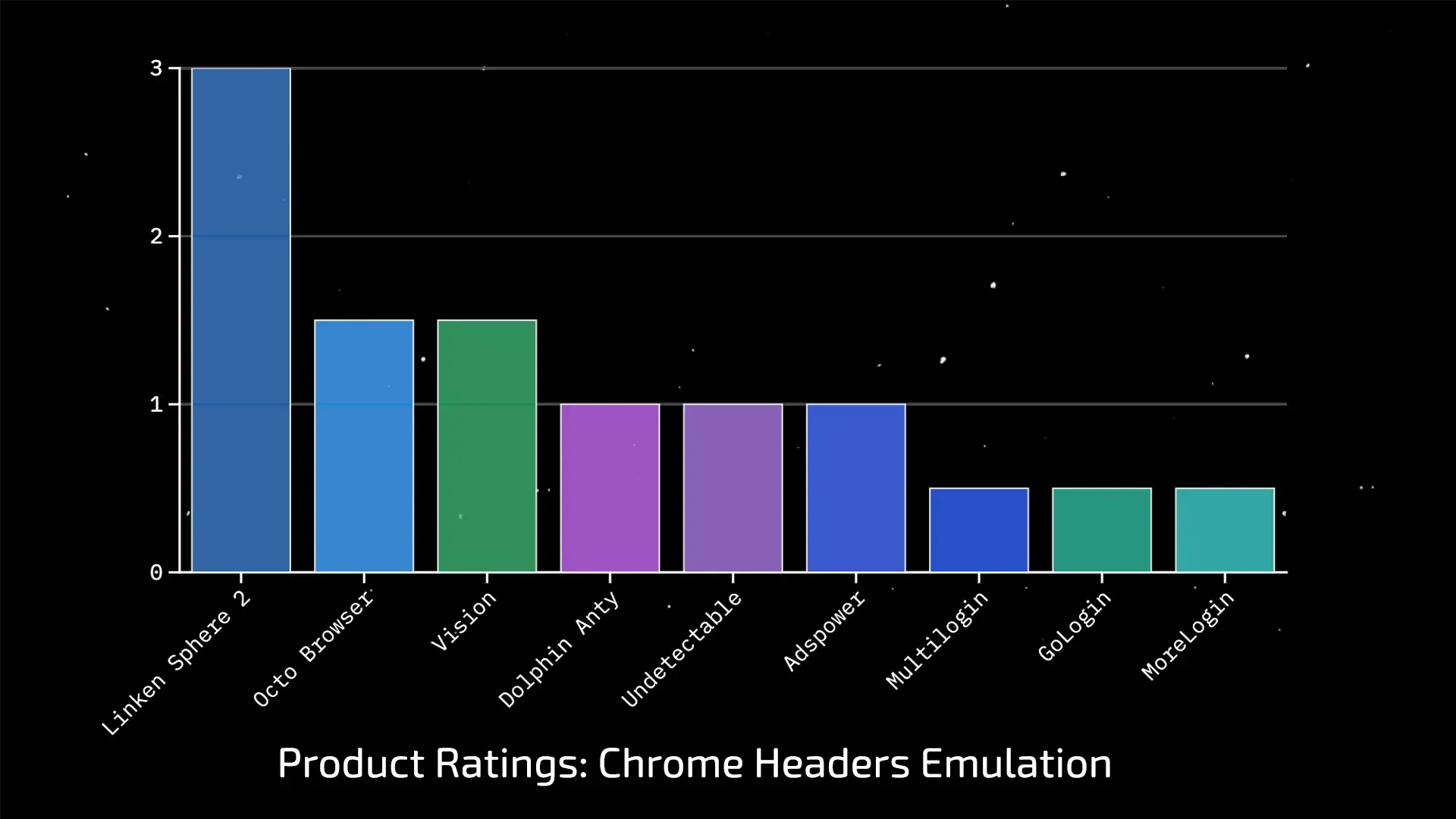
Research Results
| Product | X-Browser-* Emulation | X-Client-Data Emulation | Google Login |
| Linken Sphere 2 v2.10.11 | ✅ | ✅ | ✅ |
| Octo Browser v2.7.8 | ✅ | ⚠️ | ❌ |
| Vision v3.3.33 | ✅ | ⚠️ | ❌ |
| Dolphin Anty v2025.279.165 | ❌ | ⚠️ | ⚠️ |
| Undetectable v2.39.0 | ⚠️ | ⚠️ | ❌ |
| Adspower v7.6.3 | 2.7.8.9 | ❌ | ✅ | ❌ |
| Multilogin X Mimic 140 | ❌ | ⚠️ | ❌ |
| GoLogin v3.4.7 | ❌ | ⚠️ | ❌ |
| MoreLogin v2.42.0.0 | ❌ | ⚠️ | ❌ |
The summarized results of our research paint a clear and rather alarming picture. Behind flashy marketing promises lie fundamental conceptual flaws in implementation. To understand the depth of these issues, let’s analyze each column — each line of defense — in detail.
First Line of Defense: The Browser’s Base Signature
The four X-Browser-* headers are not just service information — they are the foundational 'signature' of modern Chrome. Their absence is an instant, obvious signal to Google’s systems that the browser is not authentic. As seen in the table, the vast majority of solutions (Dolphin Anty, Adspower, Multilogin, GoLogin, MoreLogin) simply don’t generate these headers. This is a critical error that immediately exposes a profile against real traffic, making further checks almost unnecessary.
A separate note on Undetectable: despite formally implementing these headers, in Android profiles the X-Browser-Validation field remains empty. This critical deviation from real Chrome behavior nullifies the value of their formal emulation.
Behavioral Anomaly: Static and Simplistic X-Client-Data
Here lies the key vulnerability that almost every competitor stumbles on. The problem is twofold: it’s not only about the static nature of the header but also its primitive structure.
Most solutions generate x-client-data containing only a single variation_id while completely ignoring trigger_variation_id. Meanwhile, real Chrome — simultaneously participating in dozens of 'field trials' — produces a header containing a rich set of multiple variation_id values and usually several trigger_variation_id entries.
This inherently defective and easily distinguishable fingerprint is made worse by the fact that it remains constant. Such behavior (a single ID with no updates) only occurs in a real browser during the first 10–30 seconds after launch. After that, Chrome receives updated data about active experiments from Google, and the header’s content evolves accordingly.
As a result, throughout the entire session, such a profile keeps sending an anomalous signal that can be described as: 'I am an emulator that not only does not participate in Google’s experiments but also cannot update its state.'
X-Chrome-Id-Consistency-Request as a Marker of Sync Vulnerabilities
The ability to log in to a Google account directly through the browser interface is not just convenience — it’s a key trust mechanism tightly bound to the X-Chrome-Id-Consistency-Request header. As we established earlier, this header guarantees account integrity. Accordingly, if a browser doesn’t support this feature, it physically cannot send this header, which for Google serves as direct proof of emulation.
Our tests showed that almost no solution on the market has correctly implemented this mechanism.
The only partial exception, besides Linken Sphere, is Dolphin Anty. However, its implementation only worsens the issue. By default, in a standard profile configuration, the device name transmission feature is disabled. As a result, when logging into a Google account, Dolphin does not send this critical parameter — a fundamental deviation from real Chrome behavior, which always transmits this value.
If you manually enable the DeviceName spoofing function, the system offers to generate a name — and here lies a second, equally severe flaw. The vast majority of real users never rename their devices, keeping the factory-assigned names (e.g., MacBookPro16,1, ProBook 400, VivoBook E14 E402). Instead of emulating such real-world identifiers, Dolphin’s algorithm generates linguistically unnatural names from a single machine template. During tests, we encountered examples like: BernieFast, JewellSuperTablet, KorbinUltraLaptop, MazieServer, and LiaTablet (notably, all of these appeared on PC profiles).
This is a dead, easily detectable pattern. People don’t name their devices by combining personal names with adjectives or device types. Instead of masking, this creates a unique and trackable fingerprint that not only exposes a specific profile but also allows clustering all accounts created with this tool.
The overall analysis leads to a clear verdict: these are not isolated issues but systemic vulnerabilities in the very design philosophy. Most solutions operate on a checklist principle, reproducing surface elements while completely ignoring their logic and interdependencies. For modern Google analysis systems, such omissions serve as undeniable evidence of emulation.
New Detection Vectors: Strategic Risks and Opportunities

Despite Google’s official statements about the low entropy of the X-Client-Data header, our tests — which included several hundred Chrome launches — revealed the opposite: we didn’t observe a single repetition of generated variation sets. This forces a complete reconsideration of its role in tracking mechanisms.
For ordinary users, this header becomes yet another vector for generating a unique fingerprint. Combined with IP address and device parameters, it enables precise identification of a specific browser within a network. However, for antidetect browsers, the main threat lies not in uniqueness itself, but in its poor imitation. As shown earlier, the primitive structure and static behavior of this header in most solutions represent an easily detected anomaly.
It’s important to understand the scale and intent of this data collection:
- Headers from the X-Browser-* family and X-Client-Data are sent to all Google-affiliated domains.
- The X-Chrome-Id-Consistency-Request header has a narrower purpose and is transmitted only to services directly related to authentication processes.
While these headers may not yet serve as the primary trigger for Google’s antibot systems, the current stage clearly represents mass data collection and algorithm calibration. Full-scale integration of protection systems based on these signals is the next logical step. Although the data is sent only to Google domains, it can easily be shared with partners — creating additional layers of risk.
In this new landscape, the ability to correctly authorize into a Google account from within a profile transforms from a convenience into a critical strategic asset. Proper implementation allows a session to blend seamlessly into the behavioral model of most real users, who remain logged into their browsers. This moves the profile out of the high-risk 'guest session' category and into the normal user segment — becoming a decisive factor in overall success.
Linken Sphere: Solving the Problem at a Fundamental Level
Market analysis reveals a common pattern: most solutions react post factum, adding emulation of individual elements as they are discovered. Our approach is fundamentally different. From the beginning, we viewed these mechanisms not as a set of isolated headers, but as a unified, interconnected system reflecting the internal logic of the browser. This allowed us not merely to imitate, but to recreate its behavior with native precision.
Recreating the Digital Signature: Comprehensive Header Emulation
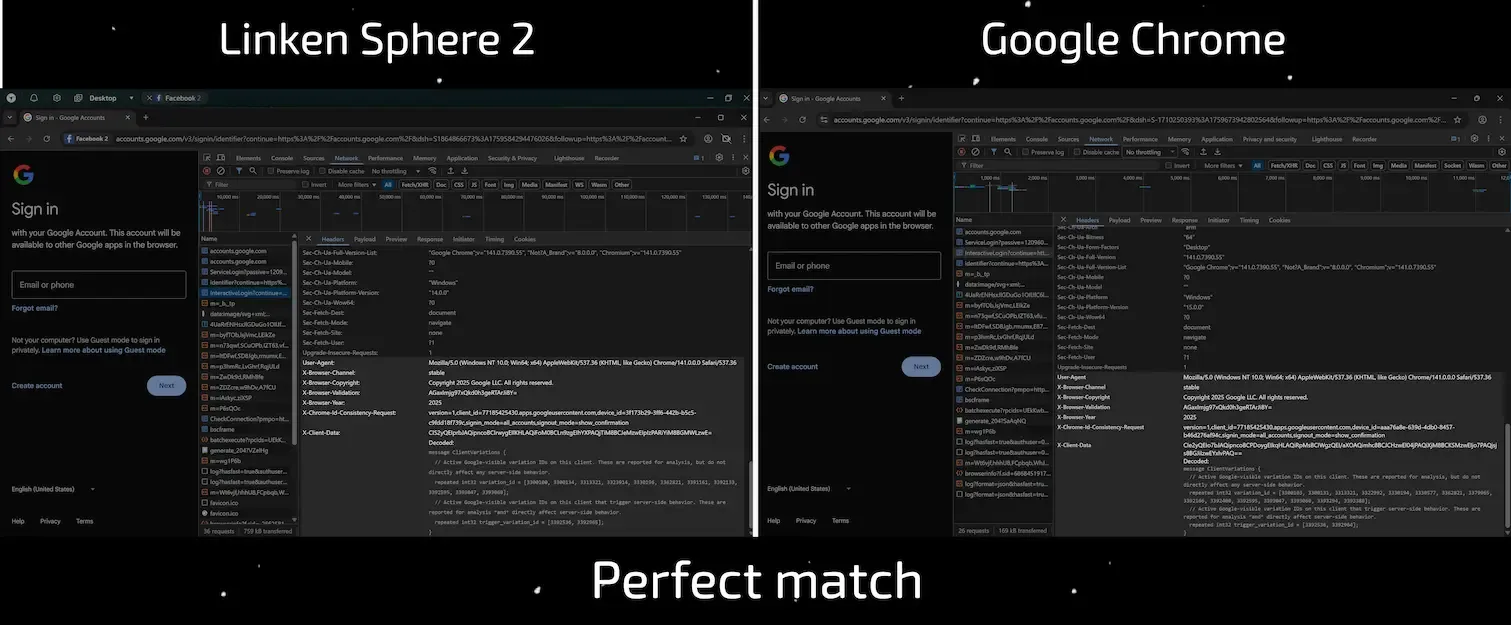
Linken Sphere implements a full, multi-layered emulation of all critical headers.
- X-Browser-* Family: This is the foundational layer of authenticity, and it is implemented flawlessly. Headers are generated correctly and fully mirror the behavior of real Google Chrome across all operating systems, including Android — where other products show clear deficiencies.
- X-Client-Data: Instead of a static, structurally primitive placeholder, Linken Sphere generates a dynamic, context-dependent header. Thanks to kernel-level substitutions, the assigned experiment IDs directly depend on the session’s configuration. The system considers device characteristics in exactly the same way as real Chrome does before assigning 'field trial' variations. This creates not just a unique, but a logically consistent fingerprint.
The Final Element of Trust: Integrated Account Synchronization
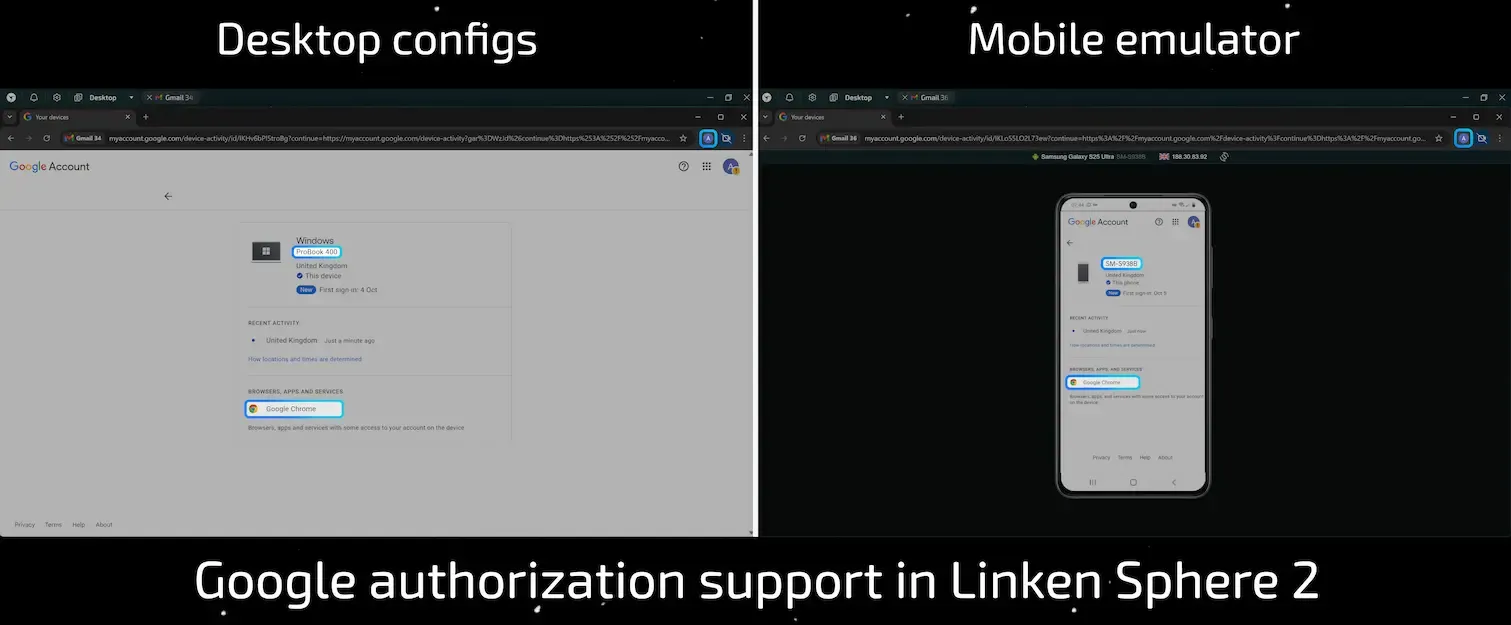
We treat the X-Chrome-Id-Consistency-Request header and its associated authorization process not as an optional feature, but as an inseparable part of a believable fingerprint.
- Integration by Default. Device name spoofing is not an optional setting that can be forgotten. It is active by default and forms a core component of the fingerprint. This ensures that the session behaves like a real device from the very first request, eliminating anomalies.
- Contextual Realism. The system generates not just random names, but fully context-accurate device identifiers. If your session emulates an HP ProBook 400, the DeviceName used will be a real one typical for that model. The same principle applies to our mobile configurations: Android profiles receive realistic names corresponding to the selected smartphone model.
The difference in approaches is fundamental. Many solutions produce a set of fragmented, easily detectable artifacts. Linken Sphere, on the other hand, creates an organic and authentic digital portrait, where every element — including the device name — is logically connected to the rest and precisely positioned.
Conclusion
Google’s introduction of proprietary HTTP headers marks a new era in the architecture of digital identification. As our research has shown, the market was unprepared for this change. Most antidetect solutions offer only superficial, fragmented emulation that collapses under serious analysis. Every incorrectly formed header and every behavioral anomaly directly lead to operational losses, starting a countdown to detection and compromise of entire account networks.
Instead of patching vulnerabilities, Linken Sphere solves the problem at its core — reconstructing a coherent, logically connected browser ecosystem. From accurate X-Client-Data generation to native Google authorization integration, every aspect works in synergy to create a truly believable and lifelike digital identity.
In this new reality, tool selection becomes critical to the stability of your operations. Stop entrusting your work to solutions lagging behind the industry. Choose the one capable of anticipating threats and providing a strategic advantage.

How to choose a CRM?
In today’s business world, the competitive environment poses significant challenges for companies in managing customer relationships. The effectiveness of these interactions affects not only profits but also reputation and future success. In this context, online CRM systems become indispensable tools for supporting and optimizing customer relationship management processes.

Using LS with OBS Studio
This is a comprehensive guide that will help you implement video stream substitution in Linken Sphere without the risk of detection by anti-fraud systems.

GermanProxy.io Review: Mobile Proxies Optimized for Linken Sphere
While large proxy providers focus on massive IP pools and broad geographic coverage, niche services can offer more tailored and exclusive options. If your workflow is tied to a specific GEO, specialized proxy providers are often the better choice — delivering better speed, higher quality, and lower cost.